Now I'm pretty sure there was a talk at BlackHat a couple of years ago about doing this, so this might not be anything new but I'll write about it anyway.
This is a great way to exfiltrate data from a network: it's stealthy (who looks at traffic going to google?), it's encrypted (the python imap and smtp library automatically handles SSL/TLS) and plus it bypasses AV completely (Pyinstaller FTW!).
The only drawback is that the compiled binary is huge: around 5MB, sometimes though that too can be a benefit since a lot of AVs won't scan files larger that a 2-3MB (unless explicitly told to do so) to increase performance!
You can get the PoC code here https://github.com/byt3bl33d3r/pyexfil
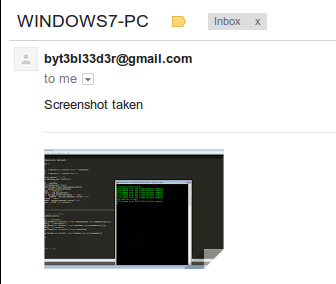
Currently it supports running os commands,running shellcode (Pyinjector style), taking screenshots, and downloading files from the victims system.
You could add a lot of functionality to this (like a keylogger if you wanted to be very evil) but for me this is just fine.
Update: Now pyexfil will send the title of the foreground window with every response!
So basically what we do is create a label called Commands; this is where pyexfil will look for new commands to execute (Duh!):
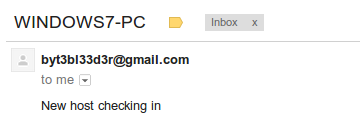
After our target checks in:
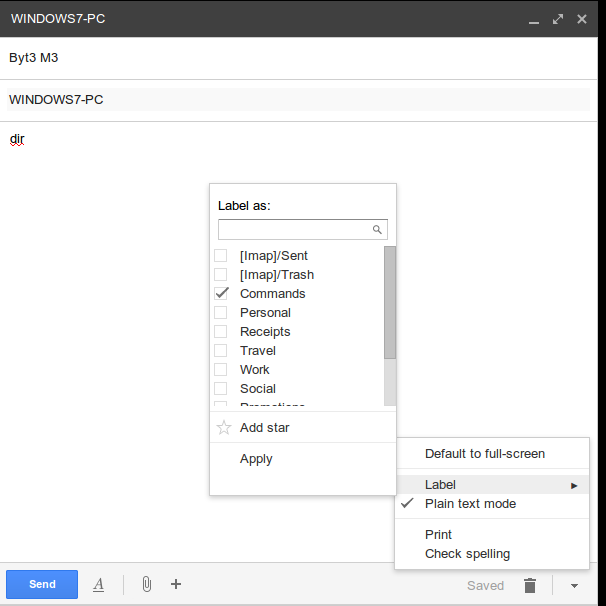
All we do is send an email to ourself with the subject line containing the hostname of our target and in the message body the command we want to execute and lable it as "Commands":
after a couple of seconds the results will be emailed back to us:
There are a few custom commands like screenshot, download and execshellcode which all do what they sound like ;)